Secure, Monitor, and Protect Your Business with Veriato Cerebral
Proactive
Defense
Prevent threats
before they happen.
Enhanced
Visibility
Gain deep insights
across all users and activities.
Operational
Efficiency
Reduce alert fatigue and
lower investigative costs.
Empower Your
Team
Help your insiders become
proactive defenders.
Stay Ahead of Insider Risk with Veriato
Insider Risk
is Growing Fast
82%
are caused by unsecure or unintentional behavior*

Containment
Takes Too Long
85 Days
average time to contain an insider incident***

Financial Impact
is Huge
95%
increase in total average costs of insider risk since 2018 **
* 2024 Data Breach Investigations Report, Verizon
** 2023 Cost of Insider Threats Global Report, Ponemon Institute
*** The Tech Report, Proofpoint
Protect Your Business from Insider Threats
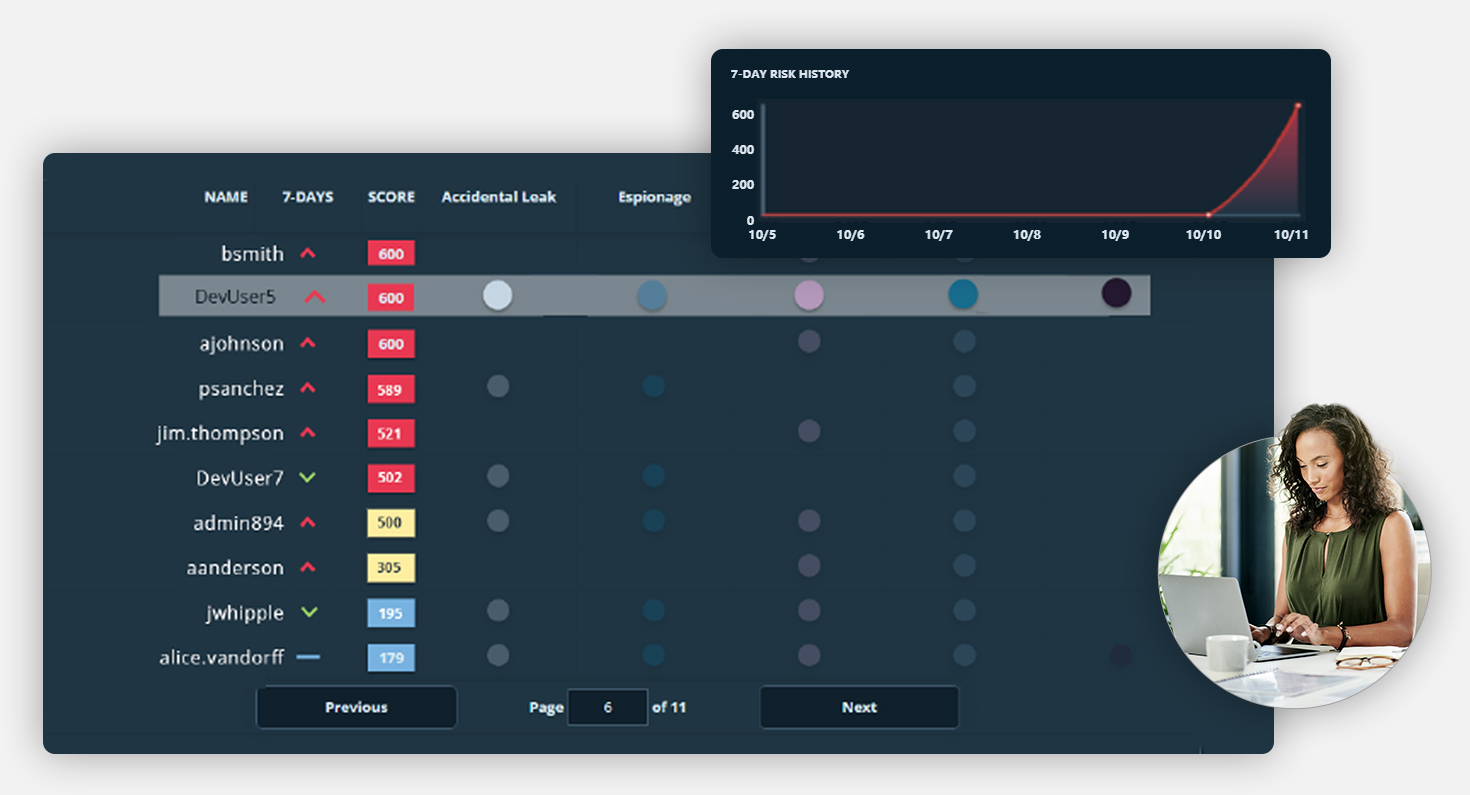
Identify Risky Behavior Patterns
Veriato provides detailed insights into user activities, including geolocation, sentiment analysis, external access, and engagement times. This comprehensive monitoring helps you maintain a holistic view of your workforce and security landscape.
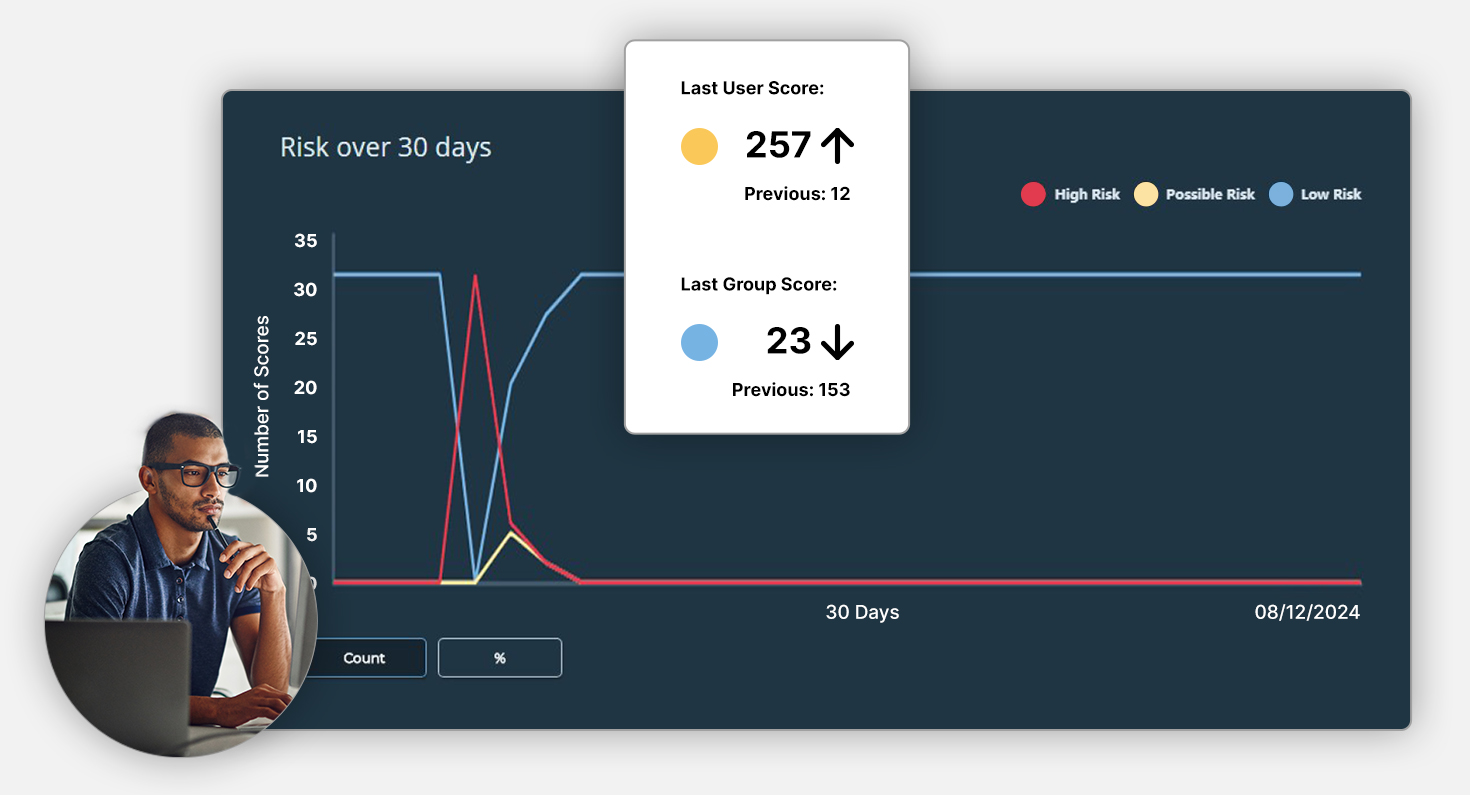
Enable Actionable Decisions
Leverage comprehensive data and insights to enable your organization to take swift, informed actions. With detailed reporting and risk analysis, Cerebral empowers leadership to prioritize and resolve critical issues effectively.
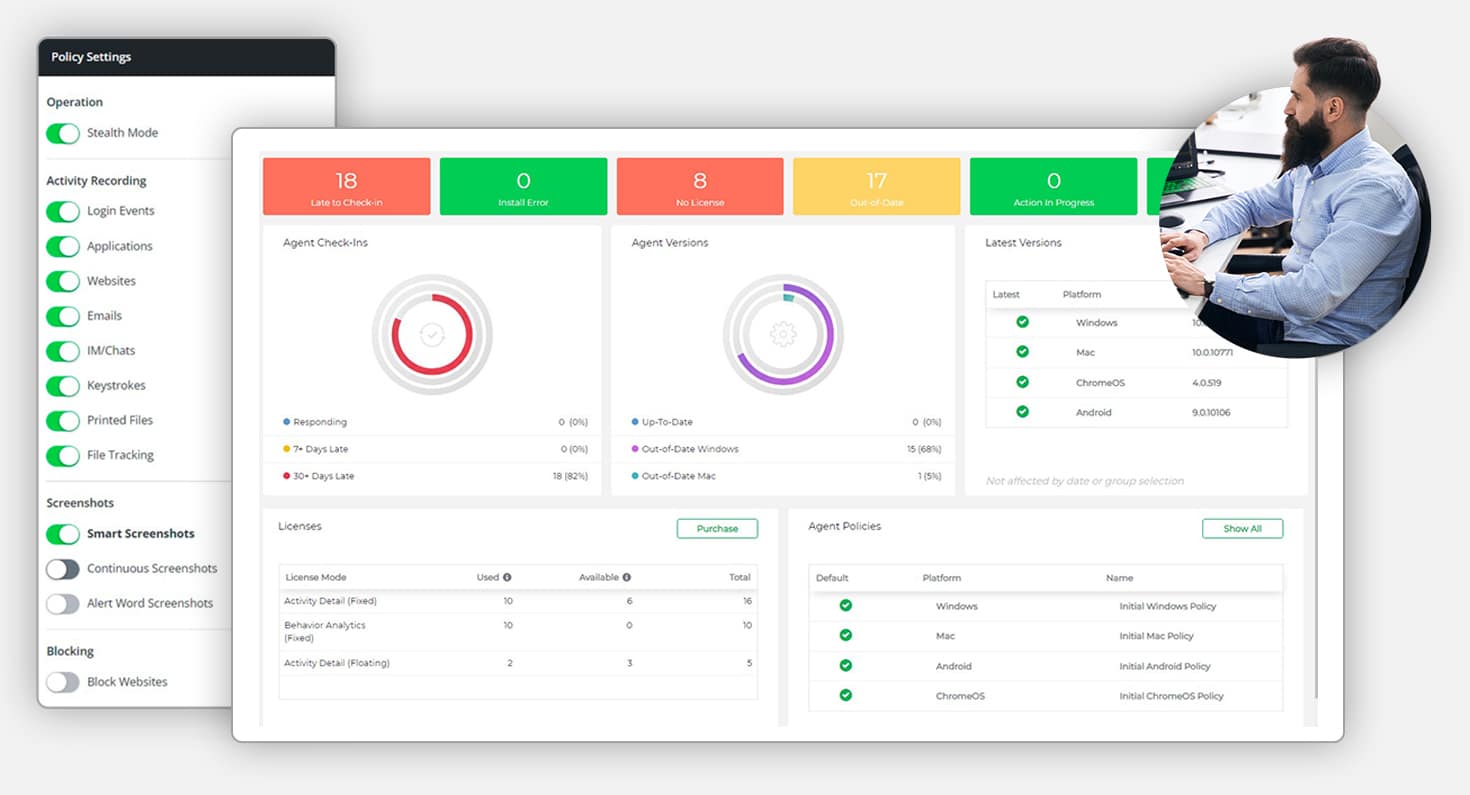
Empower Your Workforce
By identifying training gaps and offering real-time feedback, Veriato helps turn your employees into proactive defenders of your organization. This improves individual security practices and strengthens your overall compliance and security posture.
Veriato Cerebral: Power Capabilities for Insider Risk Management
Advanced User Activity Monitoring (UAM)
Monitor and record activity across devices, apps, and communications for total visibility to protect sensitive data.
AI-Powered Alerts and Reporting
Use AI-driven insights to detect unusual activity patterns with reports to mitigate risks and maintain operational continuity.
Apply AI-Driven Insider Risk Detection
Enable preventive actions, ensuring threats are addressed before they escalate and strengthen internal defenses.
Informed Decision-Making for Business Success
Provide leadership with detailed reporting that aligns with business objectives and supports strategic planning.
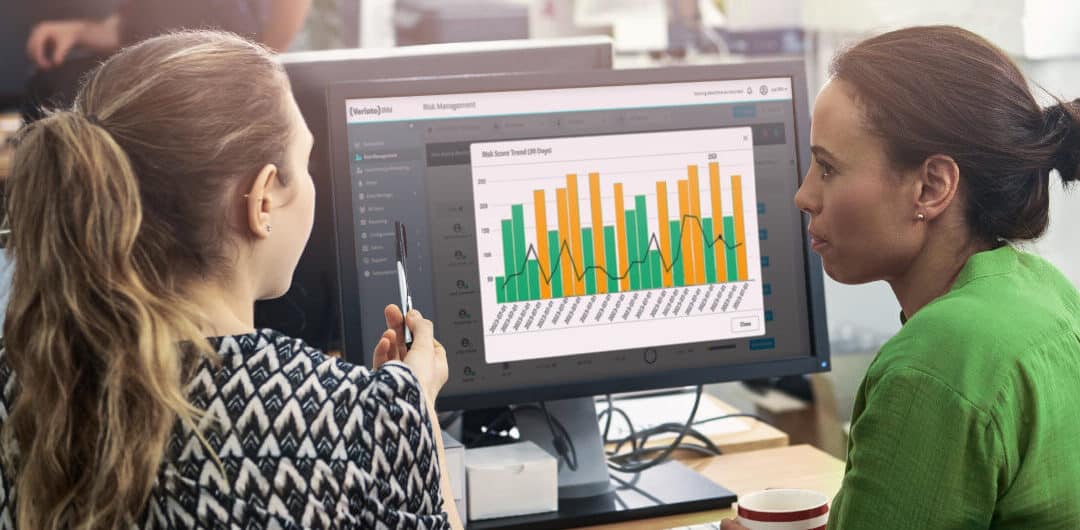
Risk Scoring for Efficiency
Understand employee risk levels based on activity and anomalies, enabling your teams to focus on the most critical threats.
Transparent and Fair Investigations
Leverage the “digital paper trail” for unbiased workplace investigations and simplify compliance audits with evidence.
What Clients Have to Say
Common Insider Risk Management Questions
Insider Risk Management Resources

Who Buys Insider Risk Management? A Business Case Across Roles
Key Takeaways: Insider Threats Are a Business Risk, Not Just a Security Concern Seventy-four percent of cybersecurity incidents originate from within the organization. Insider Risk Management (IRM) platforms help identify risks early before they escalate into...

Infographic: Seeing is Securing: The Critical Need for Visibility in Insider Risk Management
Do You Have Full Visibility to Detect and Deter Insider Risk? Insider attacks are increasing, and organizations without visibility are putting themselves at risk. The latest research reveals: 76 percent of organizations report experiencing insider threats, up from 66...
How to Predict Human Risk: Prevent Insider Threats
Predict and Prevent Human Risk Before It Becomes a Threat Insider risks account for a growing percentage of security incidents and are more challenging to detect without the right tools. With Veriato Cerebral Insider Risk Management (IRM), organizations can: Gain...




