Higher Education is Changing & Needs New Solutions

Remote & Hybrid Employee Productivity
Today’s “work from anywhere” world makes it harder for managers to keep an eye over their workforce. Unproductive employees are much more difficult to spot when your team is remote. User activity monitoring software is a way to optimize your entire workforce productivity, no matter where they work.

Sensitive Data Access & Usage
Colleges and universities need to understand detailed data usage and access by remote/hybrid employees, contractors and other third-parties. Sensitive information about financial aid, admissions and mental health has to be kept private. User activity monitoring solutions from Veriato allow detailed tracking of data being accessed to ensure security and compliance.

Policy Compliance
Higher education administrators are tasked with making sure everyone using university technology and property is following guidelines and expectations, including students using campus computers. User activity monitoring solutions from Veriato assist management in understanding application and web usage, file access and much more.
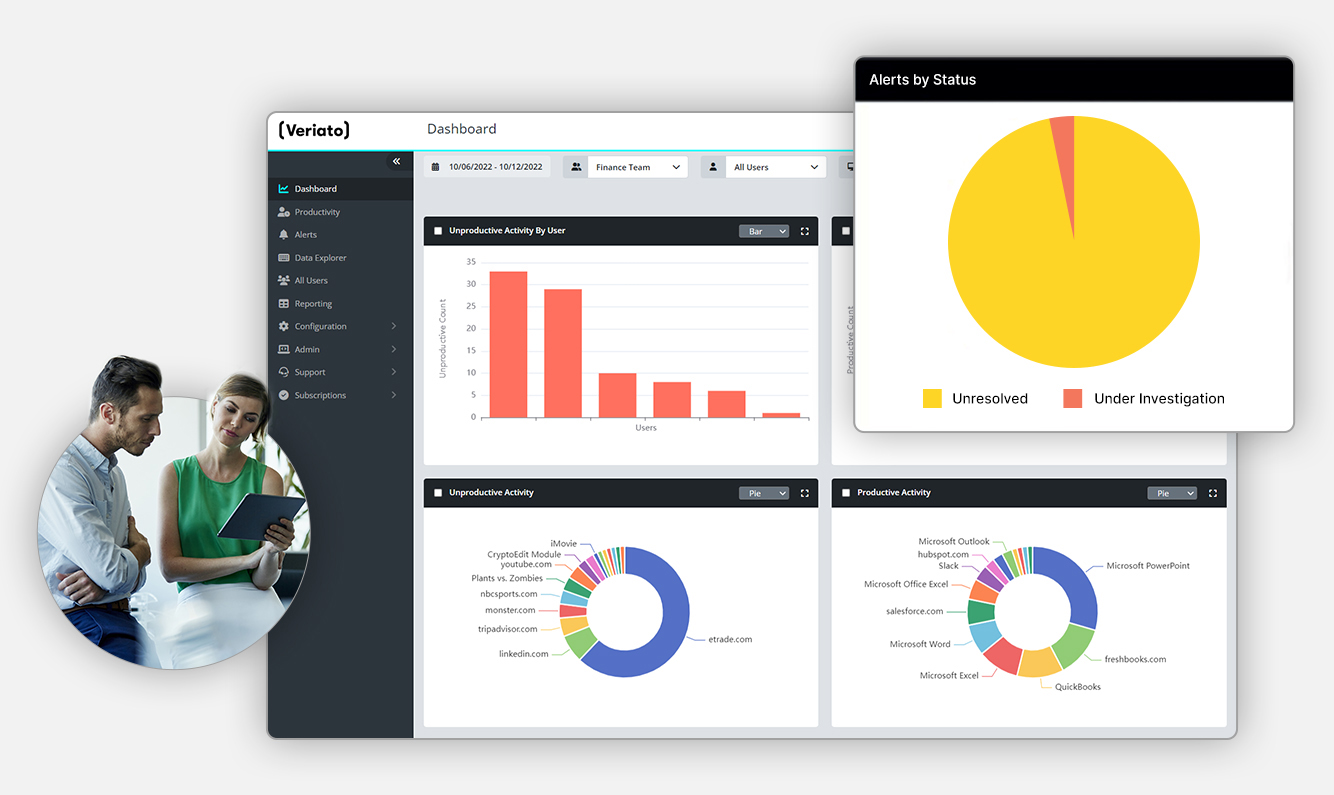
Gain Unparalleled Visibility With Veriato Employee Activity Monitoring
Keep Your Teams Productive and Critical Data Secure.
Veriato UAM helps companies thrive in today’s complex work environment, especially in industries where managers need oversight over specific teams and employees and when sensitive data and IP is at stake.
With powerful analytics that work across networks, in the cloud, and on-premise, companies gain complete visibility and understanding, ensuring maximum oversight and minimum risk.
Email & Chat Monitoring
Capture communications activity in traditional email clients as well as many popular chat and messaging applications.
Web & Application Use
Categorize websites and applications as productive or unproductive.
Screenshots
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Idle and Active Time Tracking
Track how many minutes an employee’s computer was idle or active during the workday.
File & Document Tracking
Tracks activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Network Activity
Autonomously captures connections made by applications, including ports used and bandwidth consumed.
Fully Customizable Settings
Set flexible work hours by team/department and decide when tracking starts and ends throughout the day.
Reports & Real-Time Alert
Choose from many preset reports or customize your own. Set up real-time alerts that fit your productivity metrics.
Higher Education Case Studies
University – Monitoring Staff and Students
The head of HR at a large state university ensures admin staff productivity and adherence to university policies by students and employees.
Common Employee Monitoring Questions
What Is Insider Risk Management?
Insider Risk Management is an essential approach utilized by entities to address cyber security risks presented by members of the organization with access to confidential data and systems. This strategy concentrates on detecting and handling potential dangers that insiders, such as employees or contractors, could present to information security, regulatory compliance and business continuity. It includes various measures such as observing user behaviors, managing information access, and instructing personnel on cyber security best practices.
What Insider Risk Challenges Is Higher Education Facing?
Higher education institutions encounter distinct challenges in managing insider risks, primarily due to their diverse user base comprising full-time staff, part-time workers, and even students. Each group has varying degrees of access to sensitive information stored within university systems, from personal student data to financial records. The shift towards hybrid work models adds another layer of complexity, complicating the oversight of employee productivity and the secure handling of sensitive information. This new work environment necessitates advanced strategies and solutions to effectively monitor activities and safeguard data against potential internal threats, ensuring the institution’s integrity and the privacy of its community.
What Are The Key Features of Veriato's Higher Education Solution?
Veriato provides comprehensive solutions tailored for the higher education sector, addressing the unique challenges of managing insider risks within these institutions.
- Employee Productivity & Activity Monitoring for Higher Education: Veriato’s solutions are designed to monitor all administrative staff to ensure they are focused and adhering to university policies.
- Comprehensive Solutions For Higher Education: We offer a suite of tools to monitor employee productivity, whether they are working remotely, in a hybrid model, or on-campus.
- Establish Robust Data Security Protocols: Veriato tracks application, email, and web usage, alongside file and data access, using generative AI to identify risks and prevent data breaches.
- Simplify Policy Compliance: The customizable dashboard provides essential monitoring insights, detailed user activity information, generates reports, and sets up real-time alerts.
Veriato’s solutions empower higher education institutions to monitor and manage their users efficiently, ensuring data security, policy compliance, and productivity across all types of work environments.
Why is Insider Risk Management Important in Higher Education?
In higher education, insider risk management plays a pivotal role in safeguarding confidential information, adhering to regulatory requirements, and preserving institutional integrity and public image. This approach allows universities to detect potential internal threats early and apply targeted measures to reduce risks. By implementing a comprehensive insider risk management strategy, higher education institutions can protect themselves against vulnerabilities that could compromise data security, regulatory compliance, and their reputation. This ensures a secure and trustworthy environment for students, faculty, and staff alike.
How to Get Started with Veriato?
For higher ed institutions and IT professionals interested in implementing Veriato’s insider risk management solutions, starting is straightforward:
- Assessment: Assess your existing risk environment and pinpoint particular insider threats that are pertinent to your entity. Once ready, schedule a Veriato demo.
- Implementation: Install Veriato’s specialized solutions designed to oversee, examine, and address insider behaviors efficiently.
- Training: Instruct your personnel on the significance of managing insider risks and the application of Veriato’s instruments for threat detection and reduction.
To explore further how Veriato can revolutionize your approach to insider risk management, contact us today.
Other Frequently Asked Questions
In what ways does Veriato assist universities in protecting sensitive data?
Veriato assists universities by offering comprehensive monitoring solutions that oversee user activities and data access, ensuring sensitive information such as student records, research data, and financial information is securely managed. Veriato is designed to alert administrators to any unauthorized or suspicious data handling activities.
How does Veriato ensure the privacy of monitored data within educational institutions?
Depending on the deployment option, user activity data can either be stored locally or in a secure cloud environment. AI-based OCR capabilities can be configured to remove sensitive financial or PHI data before saving. Recording policies are fully customizable and can be set up to capture different data for different teams, departments, etc.
Is Veriato’s solution flexible enough to cater to the unique needs of different departments within a university?
Veriato’s solution is flexible and scalable, designed to meet the unique security and monitoring needs of different departments within a university. Whether for administrative offices, research departments, or student services, Veriato provides tailored solutions to protect against insider threats effectively.




