The Behavioral Visibility platform built to
minimize risk and maximize productivity.
See Clearly. Act Confidently.
Category Creator. Relentless Innovator.
Veriato pioneered Insider Risk Management more than 25 years ago and now leads a new category: behavioral visibility. From advanced telemetry to AI-powered scoring, Veriato brings proactive intelligence to people-centric risk and performance challenges.
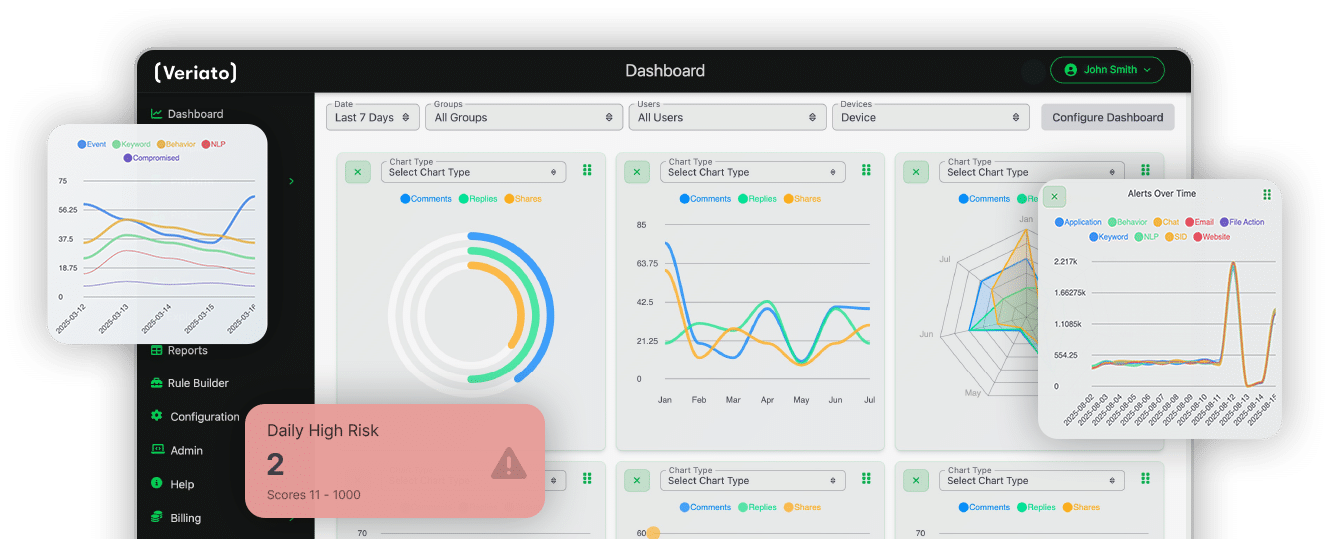
Intelligence That Powers Risk and Performance
- Tracks 130+ behavioral signals in real time
- Detects sentiment shifts, anomalies, and activity patterns
- Moves from reactive alerts to proactive, data-informed action
Behavioral Visibility
Across the Enterprise
- Security: Detects insider threats before they escalate
- HR: Surfaces disengagement, burnout, and quiet quitting
- Compliance: Simplifies audits and reinforces policy adherence
- Leadership: Delivers insight into organizational health and risk posture
One Platform.
Many Use Cases
- Legal and HR Investigations
- Compliance and Policy Enforcement
- Executive Decision Intelligence
Behavioral Intelligence that Powers Risk and Performance
Whether you’re safeguarding sensitive data or improving workforce productivity,
Veriato gives you real-time behavioral insight, powered by AI and NLP.
AI-Powered
Risk Scoring
Configurable
Monitoring Policies
Real-Time
Dashboards
Cloud or On-Prem
Deployment
Microsoft 365 + RESTful
API Integrations
Privacy-first
Design
See Risk Differently. Lead Proactively.
Organization-Wide Behavioral Visibility
Security
Finance
Legal & Compliance
Human Resources
General Management
What Clients Have to Say
Unmatched Global Reach in more than 70 countries





