The New Reality of the Public Sector

Your Agency is a Priority Target
Government agencies handle PII and other sensitive data, making them a prime target for theft. The public sector often lacks the cybersecurity capabilities and resources of private corporations. User activity monitoring and behavior analytics can give government organizations at all levels the capabilities to monitor for threats and prevent data breaches.

Sensitive Data Has Become More Accessible
With the changing nature of work, government agencies need to understand detailed data usage and access by remote/hybrid employees, contractors and other third-parties. User activity monitoring solutions from Veriato allow detailed tracking of data being accessed, applications used and much more to ensure security and compliance.

Remote & Hybrid Employee Productivity Has to be Measured
Today’s “work from anywhere” world makes it harder for managers to keep an eye over their workforce. Unproductive employees are much more difficult to spot when your team is remote. User activity monitoring software is a way to optimize your entire workforce productivity, no matter where they work.
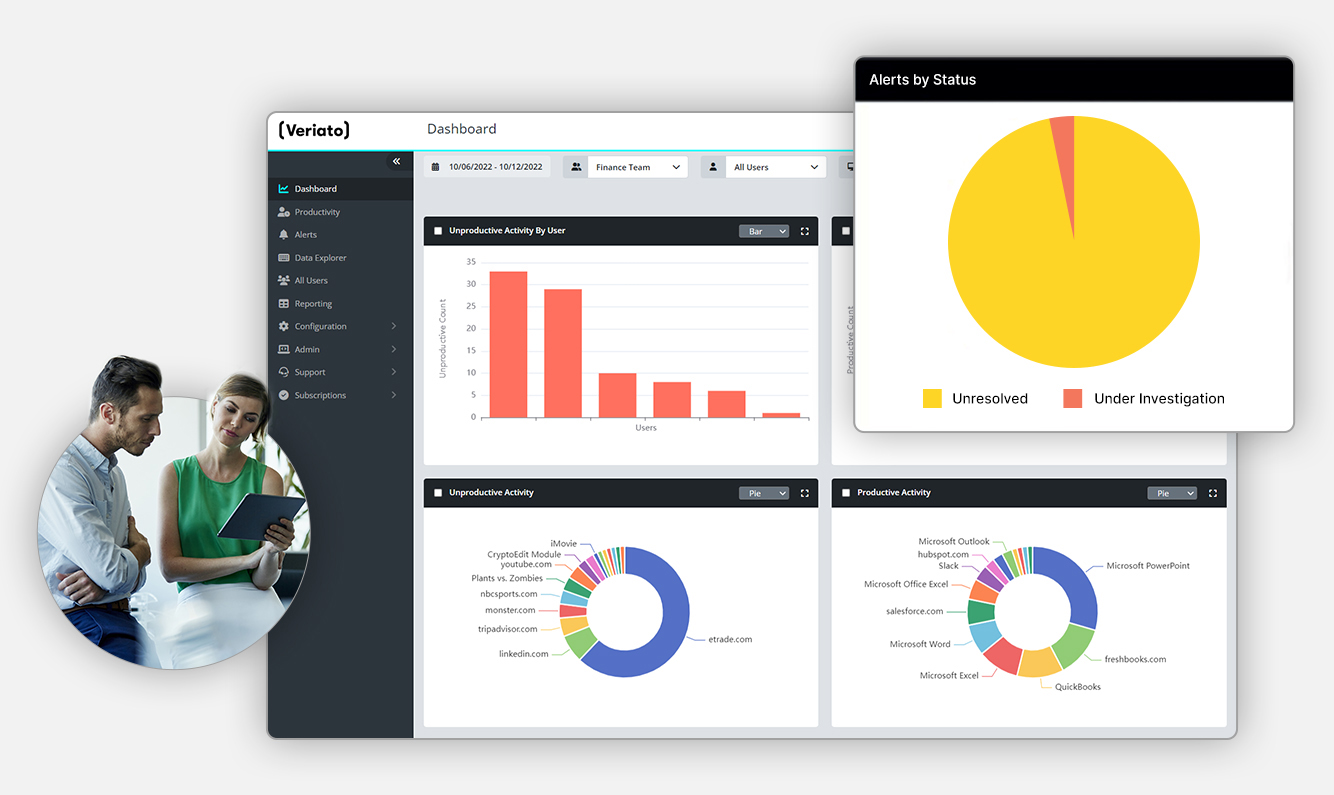
Gain Unparalleled Visibility With Veriato Employee Activity Monitoring
Keep Your Teams Productive and Critical Data Secure.
Veriato UAM helps companies thrive in today’s complex work environment, especially in industries where managers need oversight over specific teams and employees and when sensitive data and IP is at stake.
With powerful analytics that work across networks, in the cloud, and on-premise, companies gain complete visibility and understanding, ensuring maximum oversight and minimum risk.
Email & Chat Monitoring
Capture communications activity in traditional email clients as well as many popular chat and messaging applications.
Web & Application Use
Categorize websites and applications as productive or unproductive.
Screenshots
Choose between three types of screenshots: Continuous, Keyword Triggered and Activity Triggered.
Idle and Active Time Tracking
Track how many minutes an employee’s computer was idle or active during the workday.
File & Document Tracking
Tracks activities on local, removable, and cloud storage, as well as print operations. See when files are created, edited, deleted, or renamed.
Network Activity
Autonomously captures connections made by applications, including ports used and bandwidth consumed.
Fully Customizable Settings
Set flexible work hours by team/department and decide when tracking starts and ends throughout the day.
Reports & Real-Time Alert
Choose from many preset reports or customize your own. Set up real-time alerts that fit your productivity metrics.
Common Employee Monitoring Questions
What Is Insider Risk Management?
Insider risk management is a strategic approach designed to detect, prevent, and respond to cyber security threats that come from within an organization. Unlike external cyber security threats that are initiated by outsiders, insider risks involve employees, contractors, or partners who have inside information concerning the organization’s security practices, data, and computer systems. Effective insider risk management is crucial for safeguarding an organization’s critical assets, maintaining the integrity of sensitive information, and ensuring operational continuity.
What Insider Risk Challenges Are Faced In Government?
Government entities face unique insider risk challenges due to the nature of their work and the sensitivity of the information they handle. These challenges include managing access to sensitive and confidential information, detecting unauthorized data exfiltration, and preventing malicious activities by trusted insiders. The complexity of governmental structures, combined with the vast amounts of personal and sensitive data, amplifies the potential impact of insider threats.
What Are The Key Features of Veriato's Government Solution?
Veriato offers a comprehensive insider risk management solution tailored for the public sector. We leverage generative AI to help proactively detect and mitigate insider threats, ensuring robust data security and enhanced employee productivity across government entities.
- Comprehensive Solutions for the Public Sector: AI-powered algorithms analyze user behavior, identifying abnormal activity and generating individual risk scores.
- Robust Data Security Protocols: Monitors application, email, and web usage; tracks file access; generates AI-driven risk scores to protect against breaches.
- Employee Productivity Monitoring: Provides tools for managing remote, hybrid, and office teams, ensuring engagement and productivity.
With Veriato, government agencies can safeguard sensitive data, monitor employee productivity efficiently, and adapt to the evolving challenges of insider risk management in today’s digital and remote work environment.
Why is Insider Risk Management Important for the Public Sector?
-
Your Agency is a Priority Target: Government agencies, which handle personally identifiable information (PII) and other sensitive data, are prime targets for theft. The public sector’s cyber security capabilities often lag behind those of private corporations, making user activity monitoring and behavior analytics essential for detecting and preventing data breaches.
-
Sensitive Data Has Become More Accessible: With the shift towards remote and hybrid work models, understanding detailed data usage and access by employees, contractors, and third-parties is vital. Veriato’s solutions enable detailed tracking of data access and application usage to ensure security and compliance.
-
Remote & Hybrid Employee Productivity Has to be Measured: The shift to remote work has made it more difficult to oversee employee productivity. Veriato’s software addresses this challenge, allowing managers to effectively monitor and optimize the productivity of their teams, regardless of their location.
How to Get Started With Veriato?
- Government IT departments and professionals seeking to deploy Veriato’s insider risk management tools can begin effortlessly:
- Schedule a demo to explore how Veriato can help meet your unique requirements.
- Consult with our specialists to tailor the system to your agency, ensuring adherence to governmental standards while protecting against internal risks.
Other Frequently Asked Questions
What types of governmental entities can benefit from Veriato’s solutions?
Veriato’s insider risk management solutions are designed for a wide range of governmental entities, including local, state, and federal agencies. Our tools are scalable and adaptable to meet the needs of any size organization.
How does Veriato ensure the privacy of employees while monitoring their activities?
Veriato prioritizes employee privacy by adhering to strict legal and ethical standards. Our solutions are designed to monitor activities in a way that respects individual privacy rights while protecting organizational security. Customizable recording settings allow agencies to balance oversight with privacy concerns.
Can Veriato’s solutions integrate with existing governmental cybersecurity frameworks?
Yes, Veriato’s solutions can integrate with your existing cybersecurity frameworks and IT infrastructure. This ensures that agencies can enhance their insider risk management capabilities without disrupting existing security protocols.
How does Veriato handle large volumes of data for analysis and monitoring?
Veriato platform is designed to collect large volumes of data across tens of thousands of devices with minimal impact on individual endpoint performance. Your data can then be stored locally or in the cloud, depending on the time of deployment. Finally, generative AI is used to analyze the data and help prevent insider threats without a typical alert fatigue.
What training and support does Veriato offer to government agencies implementing their solutions?
Veriato provides comprehensive training and support to ensure government agencies can effectively utilize their insider risk management solutions. This includes personalized training sessions, detailed documentation, and responsive customer support to address any questions or challenges that may arise.
How does Veriato adapt to the evolving landscape of insider threats in government sectors?
By leveraging generative AI in its behavior analytics, Veriato continuously learns and improves on its predictive insider risk capabilities. This proactive approach allows Veriato to offer dynamic solutions that evolve with the changing security environment.




