Veriato Insider Risk Management Can Help Your Financial Services Organization…

Identify Risky User Behavior
Veriato applies the power of Generative AI to detect, identify and predict risky user behaviors based on user activity data, language and sentiment analysis and anomaly detection though pattern matching.

Help Prevent Costly Data Breaches
With 82% of data breaches caused by unsecure or inadvertent behavior by employees, Veriato helps prevent the most common cause of data breaches and ransomware attacks.

Cut Down Response Time
With the average time to contain an insider incident reaching 85 days, Veriato helps dramatically cut down response time by continuously capturing user activity and behavior data.
Bring the Power of Generative AI to Your Cyber Security Stack
Veriato Closes the Gap With Predictive Risk Intelligence
Veriato applies the power of Generative AI to detect, identify and predict risky user behaviors based on user activity data, language and sentiment analysis and anomaly detection though pattern matching.
Veriato IRM can proactively identify high-risk activity, analyze employee behavior and monitor your intellectual property faster and more accurately than any other solution on the market.
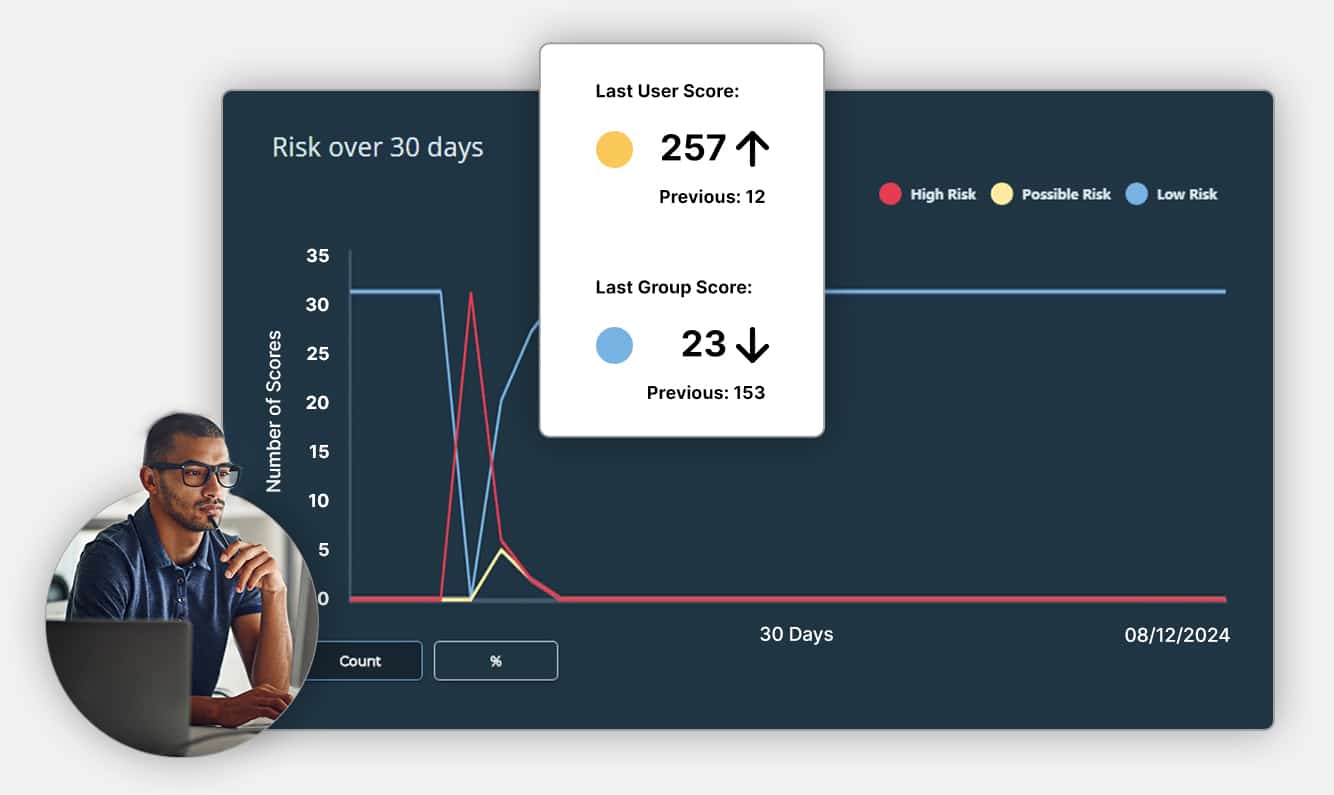
Unparalleled Risk Detection
Domain specific Generative AI trained with Retrieval Augmented Generation (RAG) for language analysis.
Complex Dimensional Analysis
Get a rich, multi-dimensional picture of user behavior with GenAI-driven Risk Scoring.
Powerful Anomaly Detection
Easily detect anomalous activity based on a rolling baseline unique to your organization.
Industry-Leading Pattern Identification
Understand and analyze patterns across logon events, document activity, email activity and much more.
Comprehensive Language & Sentiment Analysis
Detect changes in tone and sentiment with Natural Language Processing (NLP) capabilities.
Automatic PII/PHI Identification
Use RAG pre-trained models to automatically identify sensitive information on screen for alerts or reduction.
AI-Powered Threat Alerts
Minimize alert fatigue and the burden on your IT team with powerful alerts with risk score, behavior and anomaly triggers.
Flexible Deployment Options
Securely store data in the cloud, on-premise or in a hybrid cloud environment. Use regional servers to meet regulatory requirements, like GDPR.
Latest Microservices Architecture
The new microservices platform architecture allows for flexible deployment, minimal endpoint device impact and scalability to tens of thousands of endpoints.
Financial Industry Case Studies
Finance – Historical Information, Investigating an Issue Around Data Theft, Unusual Activity
A regional credit union works with Veriato to record user activity, ensure compliance and investigate data theft.
Common Employee Monitoring Questions
What Is Insider Risk Management?
Insider Risk Management is a crucial strategy employed by organizations to mitigate risks posed by individuals within the organization who have access to sensitive information and systems. It focuses on identifying and managing potential threats that insiders, whether employees, contractors, or partners, might pose to the organization’s data security, financial integrity, and operational stability. Insider Risk Management encompasses a range of practices including monitoring user activities, controlling access to information, and educating staff about security policies and procedures.
What Are Insider Threats in a Financial Institution?
The financial industry, given its reliance on vast amounts of confidential data and financial transactions, faces significant insider risk challenges. These include:
- Data Breaches: Unauthorized access to sensitive financial information can lead to significant financial loss and damage to reputation. The average cost of a breach for a financial services firm was $5.4M in 2023.
- Fraud: Insiders might misuse their access privileges for personal gain, committing fraud that can be costly to detect and rectify.
- Compliance Violations: Failure to adhere to regulatory requirements can result in hefty fines and legal consequences.
- Operational Disruption: Insider threats can disrupt operations, affecting customer trust and service delivery.
What Are The Key Features of Our Financial Industry Solution?
Veriato offers comprehensive solutions designed to help financial services firms manage and mitigate insider risks effectively. Veriato’s solutions help:
- Get Ahead of Insider Risk: Utilizing AI-powered algorithms, Veriato analyzes user behavior patterns, identifying abnormal activities and automatically alerting relevant personnel. This proactive approach ensures that any potential insider threat can be addressed promptly.
- Establish Robust Data Security Protocols: By monitoring application, email, and web usage, along with tracking file and data access, Veriato helps firms establish strong data security measures. The AI-generated risk scores are pivotal in safeguarding against data breaches and insider threats.
- Monitor User Interaction with Sensitive Data: Veriato’s solutions go beyond providing an audit trail of access to records. They enable financial firms to monitor detailed interactions with PII and other sensitive data, ensuring data security and compliance with regulatory standards.
- Demonstrate Regulatory Compliance: Financial organizations face complex compliance requirements. Veriato aids in demonstrating that effective protective controls are in place by enabling proactive monitoring, customizable alerts, and simplified reporting.
- Conduct Reviews & Audits: Veriato assists financial organizations in conducting thorough audits and addressing data breaches efficiently. By logging detailed user activity data, the software supports compliance efforts and simplifies audits. Continuous data collection and the availability of a rich data trail aid in internal investigations and audit processes.
Why is Insider Risk Management Important in the Financial Industry?
In the financial industry, where trust and integrity are paramount, insider risk management is essential for several reasons:
- Protecting Sensitive Information: Ensuring the confidentiality and integrity of customer data and financial records.
- Maintaining Regulatory Compliance: Adhering to strict industry regulations and avoiding penalties for non-compliance.
- Safeguarding Reputation: Preventing incidents that could damage the organization’s reputation and customer trust.
- Ensuring Operational Continuity: Avoiding disruptions to financial services and operations critical to customer satisfaction and business success.
How to Get Started with Veriato?
Getting started with Veriato’s insider risk management solutions involves a few key steps:
- Understand Your Needs: Assess your organization’s specific risk profile and security requirements.
- Schedule a Demo: Schedule a demo and see firsthand how Veriato can address your insider risk management needs.
- Implement Solutions: Work with Veriato’s team to implement the right solutions tailored to your organization’s unique challenges.
- Educate Your Team: Ensure that your staff is well-informed about security policies and the importance of data protection.
Other Frequently Asked Questions
What are the common signs of insider threats in the financial industry?
Common signs of insider threats include unusual access patterns or attempts to access sensitive data without a valid reason, frequent use of unauthorized external storage devices, discrepancies in financial transactions, unauthorized sharing of confidential information, and violations for company policies and security practices. Monitoring for these signs can help in early detection and mitigation of insider risks.
How can financial institutions balance employee privacy with insider risk management?
Balancing employee privacy with insider risk management involves implementing measures that are respectful of personal privacy while ensuring the security of sensitive information. This can be achieved by clearly communicating the purpose and scope of monitoring activities to employees, limiting monitoring to professional activities and areas, and ensuring that monitoring practices comply with legal requirements and ethical standards.
What role does employee training play in preventing insider threats?
Employee training is crucial in preventing insider threats. Regular, comprehensive training sessions can educate employees about the importance of data security, the potential risks associated with insider threats, and the best practices for safeguarding sensitive information. Training should also cover how to recognize and report suspicious activities, reinforcing the role of employees as a first line of defense against insider risks.
How does artificial intelligence (AI) enhance insider risk management strategies?
AI enhances insider risk management strategies by providing advanced analytics and machine learning capabilities to detect unusual patterns of behavior that may indicate insider threats. AI algorithms can analyze vast amounts of data in real-time, identify deviations from normal behavior, and automatically alert security teams to potential risks. This enables quicker responses to threats and more effective prevention of data breaches and fraud.
Can insider risk management solutions integrate with existing security systems?
Yes, insider risk management solutions can integrate with existing security systems and infrastructure. This integration allows for a unified approach to security, enhancing the ability to monitor, detect, and respond to insider threats across all systems and platforms. Integration also facilitates the sharing of intelligence and alerts between systems, improving the overall effectiveness of the organization’s security posture.




