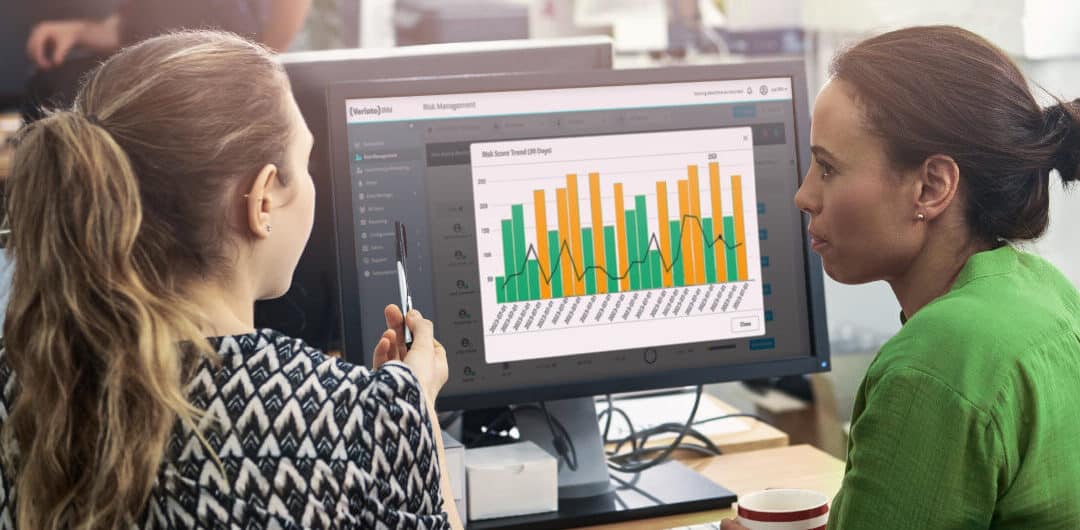
In the past, threat detection was based on delayed and reactive notifications associated with rudimentary alerting processes: A system failed, a database of your customer information was found for sale on the dark web, an employee admits to wrongdoing, and more.
Addressing these threats was a completely reactive process. The latest study by the Ponemon Institute on behalf of IBM found that the average time required to identify a data breach is 197 days. Clearly this isn’t acceptable and trans-formative security approaches need to be employed. Today, we have systems generating vast amounts of information on systems and users that can now be used in combination with artificial intelligence to predict what threats are potentially coming.
These technological advancements within the cyber security space are driving a critical shift from antiquated and reactive threat detection to modern predictive threat detection.
Get Instant access